Windows Azure Diagnostics and Trust Levels
Last week I gave a presentation on Windows Azure Diagnostics for the Azure Florida Association. You can see my blog wrap up with a list of resources and such via a previous post. In this post I’m going to answer a question that was asked at the end of my presentation.
The question was “What is the relationship between Windows Azure Trust levels and the Diagnostics module/features?” (paraphrased).
The short answer is, they aren’t related. At least they aren’t related anymore. A long while back (like SDK 1.2 or so) you had to have Full trust set to run Diagnostics in a Windows Azure web or worker role. This is no longer the case and hasn’t been for quite some time. This is the answer I provided during the presentation as well, but I dug a little deeper just to make sure I wasn’t leading people astray. If you want a more detailed explanation, then read on.
What is this Trust Level Stuff?
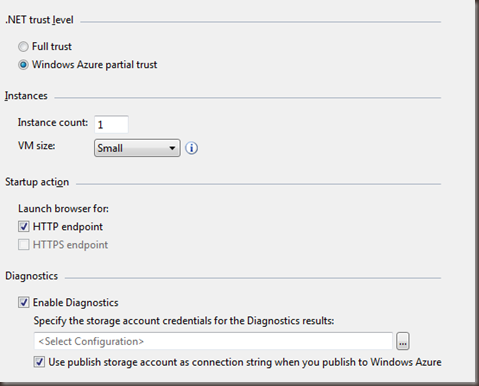
The .NET Trust level is a setting on the Web or Worker role properties under the Configuration tab, which is also the same tab that you find the Diagnostics settings for the role. Your options are either Full Trust, or Windows Azure Partial trust. By default when you create a new role the value for this setting is Full trust.
Under the hood this is modifying the service definition (csdef) file and adding an attribute named enableNativeCodeExecution to the role definition.
<WebRole name="MockingService" vmsize="Small" enableNativeCodeExecution="false">
So what does this attribute do? According to the documentation this controls the ability for native execution of code to occur and if the code runs in Full Trust or not. The documentation link above also links to a Partial Trust Policy Reference, but you’ll notice on that topic you’ll see a warning about “This topic describes a deprecated process supporting the Windows Azure SDK 1.2 and earlier”. I was unable to find anything newer, but that could just be a failure of my Bing-fu.
The Trust levels deal with Code Access Security (CAS) and controls some of the permissions that code has when it is executed. For example, if the value of the attribute is false then CAS would not allow your code to perform certain actions. Note though that as of .NET 4.0 CAS has been really moved away from so this particular setting doesn’t hold much value anymore. In the end, I can’t think of a reason to recommend changing this setting from the default now that CAS is going away.
How Did this Previously Matter?
A long time ago you when you configured Windows Azure Diagnostics you did so in code and called the DiagnosticsManager.Start method to spin things up. Back then this method actually started a process on the instance. Because of the Partial Trust/CAS settings this Start method couldn’t actually be used because starting a Process was not allowed, which meant back then you had to run in Full Trust to start Diagnostics. As I mentioned earlier, this has been changed a long time ago so, again, there is no real tie between these two settings.